Hack The Box : Delivery

This is my first writeup about how to own a box/machine in HTB. Pardon me if the steps that I’ll mention isn’t very clear. I have a lot of fun and learned a lot of things while playing this box. Hope you enjoy my writeup :D
Enumeration
The first info that I get about this machine is it’s ip adress (10.10.10.222). I want to know what services that are currently running in that ip adress, so I use Nmap to scan the ip adress and see what service that are running. The command that I use is, nmap -sV -A -T4 10.10.10.209.
-sV = Version Detection. It is used to know what is the version of service that are currently run in that network.
-A = Aggresive scan options. It enabled additional advanced and aggressive options.
-T4 = Timing template. Higher T value means faster scan. But it is also affected the scanning process quality. It is recommended to choose between T3-T4.

Now I know that the ip has a webpage access (port 80), and ssh access (port 22). I try to open the webpage, and I’ve got this page.
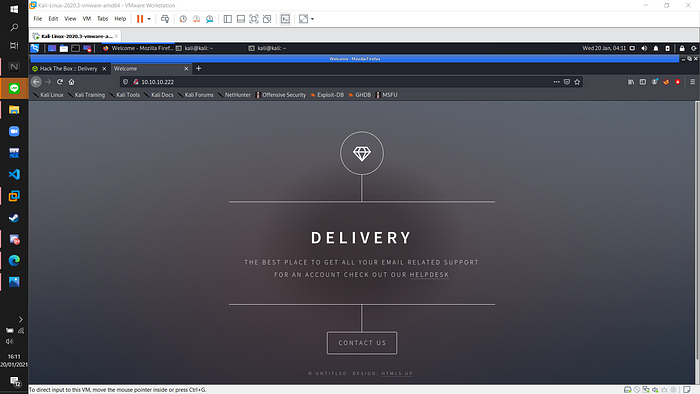
I try to gain information from the main page by accessing the source code of the website. And I found some interesting information in there.

It said that user who doesn’t have account need to access that link to register an account. So I try to access the link but I can’t because my browser doesn’t recognize the webpage that I want to visit. I use sudo nano /etc/hosts and add the ip of this machine. After that, I can access the previous page without any problem.

I try to register an account in hope that I can get something valueable from there.

After I register an account, I have some information that might be usefull. Those information are ticket id and email.

Now I try to sign in to the Delivery Support Ticket System using the account that I’ve registered before. The password to register is the ticket id that previously I’ve got from the Support Ticket Notification.
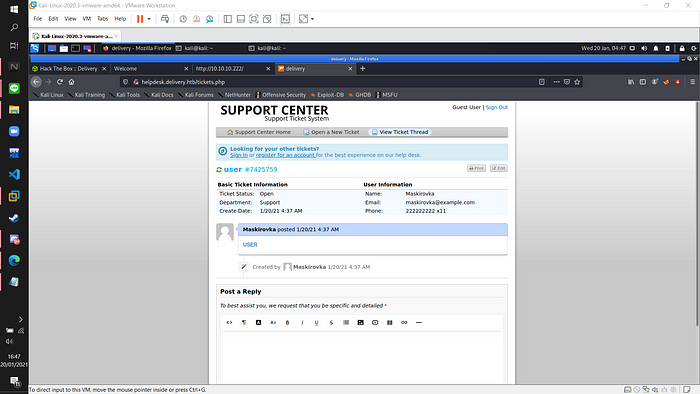
Now I have an account that are registered to the website and I’ve also got the verified email to sign up to the MatterMost website (7425759@delivery.htb). So I try to open up the mattermost website and sign up to it. If you can’t access the MatterMost website, try to adding the ip and the page that you want to access to your etc/host file.



User Flag
As you can see, now I have access to the platform that used by the team to communicate each other. The interesting info that we’ve got now is the username and password (maildeliverer, Youve_G0t_Mail!). Assuming that those are ssh username and password, I try to connect using ssh from my terminal. The command is ssh maildeliverer@10.10.10.222 (the ip might be different for each person).

And Bingo! Now I have access to the maildeliverer network using SSH. I try to find any usefull files by using ls command and I found a file named “user.txt”. I try to open the file using cat command and there it is, the user flag.

User flag : 8d189c4bd6eb9edb7afcf1f9c3bd893f
Root Flag
After getting access as a user, now I need to do another enumeration in order to get the root access. We know that this box running another service called MatterMost. So we need to search for a config file in the MatterMost directories in order to get any valuable information.

As you can see, I found the config.json file in that directory. Now we need to extract the information from that file and search for a credentials that we could use.

After analyzing for a while, I found the credentials that belong to MySql Database. Now we need to log in into that MySql service using that credentials and search for the root credentials.
username = mmuser
password = Crack_The_MM_Admin_PW

There are 2 databases that are used in this box. We’ll need to use the mattermost database, because the information_schema database is the default database and it will be a waste of time to check that. The command that I used in this terminal are:
Use mattermost;
Show tables;
Select Username,Password from Users;
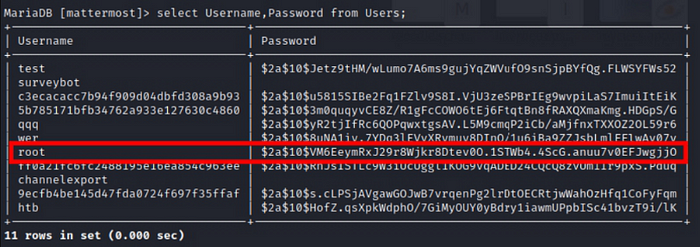
And we find a jackpot!! We found the root hash, and now what we need to do is to find a specific password that have the same hash as that one. From the previous Team Channel, we know that the password is a combination from the main word “PleaseSubscribe!”. I’ll use hashcat to make the wordlist and find the hash.
The command that I used is:
hashcat -m 3200 hash.txt word.txt -r /usr/share/hashcat/rules/best64.rule
-m = to determine the hash type that will be used. 3200 is the code for bcrypt $2*$, Blowfish hash type.
hash.txt = the hash that we wanted to find.
word.txt = the wordlist that we will be using when bruteforcing the password.
-r = flag for specify the certain rule that we will be using.

After a while, we will find the password. Now we have the root password which is PleaseSubscribe!21. Now, we just need to change user into root by using su root command and insert the password that we just found earlier.

Now we have become the root user of this box. The final thing that we need to do is just to find the root.txt and get the root hash. The root.txt file can be found at root Desktop directory.

Then we found the root hash.
Root flag: 9b6296b279271c318459c32287718f5c
And that will be our last step in pawning this box. Thank you for reading my simple writeup and have a nice day :)







